...making Linux just a little more fun!
April 2010 (#173):
- Mailbag
- 2-Cent Tips
- News Bytes, by Deividson Luiz Okopnik and Howard Dyckoff
- Magic and Mayhem, by Anonymous
- Linux's problem with Simplified Chinese, by Silas Brown
- Away Mission - Recommended for April, by Howard Dyckoff
- Pixie Chronicles: Part 1 Lessons from Mistakes, by Henry Grebler
- Yes, Master, by Henry Grebler
- Codeweavers vs. Cedega, Commercial Wine Product Comparison, by Jeff Hoogland
- Quick and Dirty Web Filtering on Linux, by Anderson Silva
- Picking Fruit, by Ken Starks
- XKCD, by Randall Munroe
- Doomed to Obscurity, by Pete Trbovich
- The Linux Launderette
Mailbag
This month's answers created by:
[ Anderson Silva, Steve 'Ashcrow' Milner, Amit Kumar Saha, Ben Okopnik, Karl-Heinz Herrmann, René Pfeiffer, Mulyadi Santosa, Neil Youngman, Steve Brown ]
...and you, our readers!
Gazette Matters
Official Twitter?
Amit Saha [amitsaha.in at gmail.com]
Tue, 23 Mar 2010 15:01:10 +0530
Hi TAG:
Is this the official LG twitter a/c: http://twitter.com/linuxgazette ?
-Amit
--
Journal: http://amitksaha.wordpress.com,
µ-blog: http://twitter.com/amitsaha
[ Thread continues here (6 messages/4.67kB) ]
Oh, one more thing...
Ben Okopnik [ben at linuxgazette.net]
Mon, 1 Mar 2010 11:53:35 -0500
...has anyone noticed anything different about TAG? No? Good. 
The Answer Gang list - in fact, all the LG lists - have now been
rehosted, and everything seems to be working fine (LG itself is still
hosted where it was, due to the kind offices of Thomas Fullhart of
Fullhart Software, http://fullhartsoftware.com/). That's a very large
load off my mind, and much thanks to René Pfeiffer whose help in this
move made the list transition much, much easier.
There's something I'd like to mention at this point; something really
important, and something that I'm going to cover in this month's Back
Page in LG. It's a change in policy - one of those things that I do
only on occasion, and not simply when it's warranted but when it's
required. Experience has shown that it is, indeed, required.
The addition to our policy is a simple one: Be nice. Be polite. Bastard
Operators from Hell are explicitly unwelcome. No rudeness is allowed in
LG from here forward - and this is the way it'll stay as long as I'm
EiC, and as long as I'm associated with LG in any way.
The recent flamewar here in TAG has convinced me that this needs to be
a hard limit, for my own sake as well as that of everyone else. I've
let my temper get away from me here in the past, and that's no more
acceptable than it is for anyone else to do so.
René has agreed to serve as the TAG moderator, and I'm as much subject
to his decisions as anyone else. As for the broader issue of LG itself,
my interpretation of this policy is "no more ranting (humor excepted)"
in the articles.
Whatever went on in the past, I want every aspect of LG to be that of a
pleasant, professional environment - for our staff as well as our
readers. Suggestions for making it more so are always welcome.
--
* Ben Okopnik * Editor-in-Chief, Linux Gazette * http://LinuxGazette.NET *
[ Thread continues here (3 messages/3.09kB) ]
Our Mailbag
Weird networking question
Deividson Okopnik [deivid.okop at gmail.com]
Fri, 19 Mar 2010 11:00:53 -0300
Hello TAG!
I have an unusual networking problem to solve here, and I'm needing some help.
Basically I got a machine with 2 network interfaces, eth0 and eth1,
and both are connected in the same hub.
But eth0 has the ip 192.168.0.97, and doesnt need a proxy to access
the internet.
Eth1's ip is 192.168.0.200, and that IP needs a proxy to access the
internet (and several sites are blocked, etc).
Alls configured, but it seems that everything's trying to use the eth1
to access the internet, and I need it to be accessed using eth0.
Everything should use eth0, I just need eth1 to be used for apache and mysql...
Any clue on how to configure that?
Thanks
Deividson
[ Thread continues here (12 messages/12.93kB) ]
Backup Strategy
Amit Saha [amitsaha.in at gmail.com]
Sat, 6 Mar 2010 20:29:43 +0530
Hello all:
I have a simple requirement- I want to back up all my lab's data (~
1TB and increasing) to a 2TB hard-disk on another machine. How best
should I partition/create volumes on my 2 TB hard-disk so as to enable
my backups? I have no special requirements. Just simple dumping of the
contents from one to another. In the same vein, I would like to hear
how you do something similar.
(I plan to use rsync for the same)
Best,
Amit
--
Journal: http://amitksaha.wordpress.com,
µ-blog: http://twitter.com/amitsaha
Freenode: cornucopic in #scheme, #lisp, #math,#linux, #python
[ Thread continues here (11 messages/11.89kB) ]
Rabbit Vcs
Jimmy O'Regan [joregan at gmail.com]
Fri, 19 Mar 2010 19:08:43 +0000
http://www.rabbitvcs.org/
TortoiseSVN clone for gnome - great for anyone who is not a version
control ninja, but would like to play one on TV
Talkback: Discuss this article with The Answer Gang
Published in Issue 173 of Linux Gazette, April 2010
2-Cent Tips
Two-cent Tip: Yo! zdump!
Ben Okopnik [ben at linuxgazette.net]
Sun, 14 Mar 2010 23:43:47 -0400
----- Forwarded message from "s. keeling" <keeling@nucleus.com> -----
I've yet again just discovered that tomorrow morning is "spring
forward Day", so this may be apropos:
alias dst="zdump -v Canada/Mountain | grep $(date '+%Y')"
Substitute your TZ for C/M, of course. Submit to 2cT?
--
* Ben Okopnik * Editor-in-Chief, Linux Gazette * http://LinuxGazette.NET *
[ Thread continues here (7 messages/6.86kB) ]
Two-cent Tip: VirtualBox Tricks?
clarjon1 [clarjon1 at gmail.com]
Thu, 25 Mar 2010 09:20:19 -0400
Hey Gang!
I don't know how many of you use VirtualBox (OSE or otherwise), but I
was wondering if any of you had any cool tricks-of-the trade that
perhaps readers might be able to use.
To start off with, here's one that makes VBox really easy for my mom
to use, a little something I've called the "XP Start Button":
It's essentially an icon on the desktop/menu entry. I've upgraded her
laptop to find that she's never ever had a need to boot up windows,
but unfortunately the tax guy wants her to run windows specific
software.
Anyways, here's the tip:
Create a .desktop file in a folder/desktop, and fill it with the following:
[Desktop Entry]
Encoding=UTF-8
Version=1.0
Type=Application
Terminal=false
Name[en_US]=Windows XP
Exec=VirtualBox --startvm "Windows XP"
Name=Windows XP
Of course, replacing the name of the virtual machine with the one you
wish to start on opening of the .desktop file.
Hope to hear more tips, wonder what tweaks i might learn 
Talkback: Discuss this article with The Answer Gang
Published in Issue 173 of Linux Gazette, April 2010
News Bytes
By Deividson Luiz Okopnik and Howard Dyckoff

|
Contents:
|
Selected and Edited by Deividson Okopnik
Please submit your News Bytes items in
plain text; other formats may be rejected without reading.
[You have been warned!] A one- or two-paragraph summary plus a URL has a
much higher chance of being published than an entire press release. Submit
items to bytes@linuxgazette.net. Deividson can also be reached via twitter.
News in General
 Debian Kernel Vulnerabilities Being Patched
Debian Kernel Vulnerabilities Being Patched
Several long term kernel security vulnerabilities affecting Debian
distros, including Ubuntu, are being addressed after receiving several
CVE citations. The vulnerabilities are in the more recent Debian
distros, including Lenny, Etch, and Squeeze. They also cover the
following Ubuntu releases:
- Ubuntu 6.06 LTS;
- Ubuntu 8.04 LTS;
- Ubuntu 8.10;
- Ubuntu 9.04;
- Ubuntu 9.10.
The vulnerabilities involve Denial of Service attacks and, in at least
one case, privilege escalation. One CVE involves an attacker
accessing a VM guest doing a DOS attack on the host machine. The CVE
numbers involved are: CVE-2010-0307, CVE-2010-0309, CVE-2010-0410,
CVE-2010-0415, CVE-2010-0622 and CVE-2010-0623.
More details are here: http://www.ubuntu.com/usn/USN-914-1/.
CVE is a list of information security vulnerabilities and exposures
that aims to provide common names for publicly known problems. The
goal of CVE is to make it easier to share data across separate
vulnerability capabilities (tools, repositories, and services) with
this "common enumeration".
 Metrics Reveal "Most Powerful Voices in Open Source"
Metrics Reveal "Most Powerful Voices in Open Source"
In March, MindTouch, an open source alternative to Microsoft
SharePoint, announced the publication of the "Most Powerful Voices in
Open Source" (MPV) ranking. The list presents the top 50 most vocal,
followed, and repeated/re-posted open source commentators, representing
several spheres of influence, including media, vendors, OSS projects,
standards bodies, community management, and more.
Created by MindTouch, the MPV ranking draws from the wide array of
metrics available through Web and Enterprise 2.0 channels, including
Twitter, Google News alerts, unique online visitor counts and analysis
of the related "buzz" of vendor/project affiliations. This compilation
was created using the MindTouch platform, federating these data
sources, applying varied weighting, and processing it for delivery of
the ranking. The list, which includes members worldwide from
organizations such as Ars Technica, Canonical, Google, and
SpringSource, is available in its entirety here:
http://www.mindtouch.com/blog.
The top 5 MPVs are:
- Tim O'Reilly, founder and CEO of O'Reilly Media;
- Linus Torvalds, founder of Linux, open source advocate;
- Chris Messina, open Web advocate, Google;
- Miguel de Icaza, founder, Mono and Gnome projects;
- Jonathan Schwartz, former CEO of Sun Microsystems.
"It's about time someone has put together a metrics-based ranking of
open source influencers," said Larry Augustin, CEO of SugarCRM.
"Community advocacy is the major thrust of the spirit of open source,
and communities have leaders. This list does a great job of
identifying those leading voices."
"You'll see that this ranking is no popularity contest, there are a
number of surprises outside of the 'usual suspects' often seen on this
type of list," said Aaron Fulkerson, CEO of MindTouch. "This is
because we let the numbers do the talking, instead of an
emotions-based market perception that too frequently comes into play."
MindTouch is a leading provider of enterprise collaboration solutions
in a market where more companies are operating under "lite" IT
budgets. The purpose of MindTouch is to provide wiki-like ease of
collaboration between humans and machines. For more information,
please visit http://www.mindtouch.com/.
 Linux Foundation to Host MeeGo Project
Linux Foundation to Host MeeGo Project
The Linux Foundation will be hosting the MeeGo project, an open source
software platform for mobile computing devices. MeeGo combines Intel's
Moblin and Nokia's Maemo projects into one common Linux-based platform.
MeeGo, announced in February by Intel and Nokia, will be deployed
across many computing device types - including mobile computers, media
phones, connected TVs, and in-vehicle infotainment systems. MeeGo is
designed from the ground up for a new class of interactive computing
devices.
MeeGo will be hosted by the Linux Foundation as an open source project
in line with the best practices of the open source development model.
MeeGo is working with existing upstream projects such as the Linux
kernel, ofono, connman, X.org, D-BUS, tracker, GStreamer, Pulseaudio,
and others. The companies and projects associated with MeeGo will
continue to support those upstream projects.
As an open source software platform, MeeGo will help to reduce market
fragmentation and complexity. Along with MeeGo, the Linux Foundation
is working with companies and projects to optimize best practices for
Linux-based development and lower costs for companies using
Linux-based mobile operating systems. More information can be found at
http://www.linuxfoundation.org/embedded/.
MeeGo and other Linux embedded issues will be discussed at the
upcoming Linux Foundation Collaboration Summit in San Francisco. More
information on the meeting can be found at
http://events.linuxfoundation.org/.
The Linux Foundation's MeeGo project welcomes contributors and
encourages developers and others to get involved at the site or find
out more about joining the Linux Foundation at
http://www.linuxfoundation.org/meego/. Moblin and Maemo contributors
are encouraged to participate at http://www.meego.com/.
 Linux Foundation Launches Free Training Webinars for Linux Pros
Linux Foundation Launches Free Training Webinars for Linux Pros
Starting in March, the Linux Foundation has been offering free Linux
Training webinars taught by well-known Linux developers. This is an
opportunity to learn directly from key developers and to sample some
of the courses offered through their Linux training program.
Here's a list of upcoming training webinars:
- "How to Work with the Linux Community" by LWN.net editor and kernel
developer Jon Corbet;
- "Introduction to Embedded Linux" by author Jerry Cooperstein;
- "An Introduction to Git" by kernel maintainer and TAB chair James
Bottomley;
- "Linux System Troubleshooting and Tuning" and "Linux Administration
101" by Linux author and community manager Joe "Zonker" Brockmeier;
- "Linux Filesystem Overview" and "Linux Virtualized Storage" by
kernel developer Christoph Hellwig;
- "Btrfs: An Intro and Update" to the new file system by project lead
Chris Mason;
- "Linux Performance Tuning" by kernel developer Ted Ts'o.
The Linux Foundation is also adding sessions for those interested in
embedded Linux development. This is from Amanda McPherson's Linux
Foundation blog:
"...we announced a free webinar series to help connect developers to
the experts they need to advance their careers. Based on the demand
we're seeing in light of these recent announcements, we are announcing
a new free training webinar on embedded Linux. In this free webinar,
you will receive the basics of embedded Linux development and get an
overview of best practices. This is a fantastic opportunity to learn
about a very hot area in technology."
More information is available here:
http://training.linuxfoundation.org/lp/sign-up-for-the-free-linux-training-webinar-series.
 IBM Launches Development & Test Cloud Utilizing Red Hat Technology
IBM Launches Development & Test Cloud Utilizing Red Hat Technology
IBM has selected Red Hat Enterprise Virtualization as a platform in
its new cloud computing service for development and test. This
means that the Red Hat Enterprise KVM Hypervisor Technology is a
major part of the IBM Cloud.
"Our decade-long partnership with Red Hat has always been focused on
customer value and innovation. Today, we are extending this
partnership to include cloud computing..." said Maria Azua, vice
president of Cloud Computing Enablement at IBM. "Red Hat Enterprise
Virtualization is an optimal hypervisor technology for the
infrastructure offerings on the IBM cloud."
Red Hat first announced plans to deliver Red Hat Enterprise
Virtualization in February 2009. In November 2009, Red Hat Enterprise
Virtualization for Servers was released, providing its customers with
a cost-effective choice in the virtualization market. Red Hat
Enterprise Virtualization offers very recent technology for the
deployment of open cloud computing infrastructures.
Scott Crenshaw, vice president and general manager, Cloud Business
Unit at Red Hat said, "Together, Red Hat and IBM aim to break down
barriers to virtualization and cloud adoption by providing customers
with a stable and robust environment to meet their enterprise
applications requirements. We believe that combining Red Hat
Enterprise Virtualization software with IBM's server, storage and
network hardware, plus IBM's well-known enterprise support and
services, as the foundational components of IBM's cloud infrastructure
offers a compelling application environment for customers".
For more information about Red Hat and cloud computing, visit
http://www.redhat.com/solutions/cloud/.
For more information about IBM's cloud computing products and
services, visit http://www.ibm.com/cloud/.
Conferences and Events
- User2User - Mentor Graphics User Group
-
April 6, Marriott Hotel, Santa Clara, CA
http://user2user.mentor.com/.
- Ethernet Europe 2010
-
April 12 - 13, Marriott Grosvenor Square, London, UK
http://www.lightreading.com/live/event_information.asp?event_id=29206/.
- Black Hat Europe 2010
-
April 12 - 15, Hotel Rey Juan Carlos, Barcelona, Spain
http://www.blackhat.com/html/bh-eu-10/bh-eu-10-home.html.
- Texas Linux Fest
-
April 10, Austin, TX
http://www.texaslinuxfest.org/.
- MySQL Conference & Expo 2010
-
April 12 - 15, Convention Center, Santa Clara, CA
http://post.oreilly.com/rd/9z1zsrga27oif4odllegr62hds4rs0sg7jrfo5r0b28/.
- 4th Annual Linux Foundation Collaboration Summit
-
co-located with the Linux Forum Embedded Linux Conference
April 14 - 16, Hotel Kabuki, San Francisco, CA
[by invitation only]
- eComm - The Emerging Communications Conference
-
April 19 - 21, Airport Marriott, San Francisco, CA
http://america.ecomm.ec/2010/.
- Cloud Computing Conference / Virtualization Conference
-
April 19 - 21, Javits Convention Center, New York, NY
http://cloudcomputingexpo.com/.
- STAREAST 2010 - Software Testing Analysis & Review
-
April 25 - 30, Orlando, FL
http://www.sqe.com/STAREAST/.
- Usenix LEET '10, IPTPS '10
-
April 27, 28 - 30, San Jose, CA
http://usenix.com/events/.
- USENIX Symposium on Networked Systems Design & Implementation (USENIX NSDI '10)
-
April 28 - 30, San Jose, CA
At NSDI '10, meet with leading researchers to explore the design
principles of large-scale networked and distributed systems. This
year's 3-day technical program includes 29 technical papers with
topics including cloud services, Web browsers and servers, datacenter
and wireless networks, malware, and more. NSDI '10 will also feature a
poster session showcasing early research in progress. Don't miss this
unique opportunity to meet with premier researchers in the computer
networking, distributed systems, and operating systems communities.
Register by April 5 and save! Additional discounts are available!
http://www.usenix.org/nsdi10/lg/

http://www.usenix.org/nsdi10/lg/
- Citrix Synergy-SF
-
May 12 - 14, San Francisco, Ca
http://www.citrix.com/lang/English/events.asp.
- Black Hat Abu Dhabi 2010
-
May 30 - June 2, Abu Dhabi, United Arab Emirates
http://www.blackhat.com/html/bh-ad-10/bh-ad-10-home.html.
- Southeast Linuxfest (SELF 2010)
-
June 12 - 13, Spartanburg, SC
The Southeast LinuxFest is a community event for anyone who wants to
learn more about Linux and Free & Open Source software. It is part
educational conference, and part social gathering. Like Linux itself,
it is shared with attendees of all skill levels to communicate tips and
ideas, and to benefit all who use Linux/Free and Open Source Software.
The Southeast LinuxFest is the place to learn, to make new friends, to
network with new business partners, and most importantly, to have fun!
Register today (FREE to attend)! Book your hotel room now and save!
http://www.southeastlinuxfest.org/registration/form/

http://www.southeastlinuxfest.org
- Über Conf 2010
-
June 14 - 17, Denver, CO
http://uberconf.com/conference/denver/2010/06/home/.
- Semantic Technology Conference
-
June 21 - 25, Hilton Union Square, San Francisco, CA
http://www.semantic-conference.com/.
- O'Reilly Velocity Conference
-
June 22 - 24, Santa Clara, CA
http://en.oreilly.com/velocity/.
Distro News
 NexentaStor Community Edition 3.0 Released
NexentaStor Community Edition 3.0 Released
NexentaStor Community Edition 3.0 has been released. This release stems
from the combined community efforts of Nexenta Partners and Nexenta
users.
Now with many new features, NexentaStor CE is called the 'most complete'
and feature-rich free unified storage solution.
This is a major NexentaStor release, with improved hardware support and
many bug fixes.
Summary of New Features:
- ZFS additions: Deduplication (based on OpenSolaris b134);
- Free for up to 12 TB of 'used' storage;
- Community edition supports easy upgrades;
- Many new features in the management interface;
- Integrated search.
Get the ISO and also the VMware releases here:
http://www.nexentastor.org/projects/site/wiki/CommunityEdition/.
 openSUSE 11.3 Milestone 4 Release
openSUSE 11.3 Milestone 4 Release
The fourth of seven scheduled milestone releases for 11.3 was completed
and released on schedule. Milestone 4 focuses on switching to upstart as
init daemon.
Here are some updates in the new release:
- OpenOffice.Org has been updated to 3.2.1 Beta1 with new features;
- NetworkManager has been updated to version 0.8;
- The conntrack-network filtering system has been added. These
are userspace tools that allow system administrators interact with the
Connection Tracking System, which is the module that provides stateful
packet inspection for iptables;
- The Mono stack has been updated to release 2.6.3 together with
monoDevelop 2.2.2;
- The Moblin team has started with the integration of the Moblin
UI into the distribution and plan to have everything ready for the
next milestone;
- The LiveCDs have virtualbox guest tools. Now features like
screen resizing, seamless mode, and shared clipboards work
automatically after boot-up.
Grab the milestone release from http://software.opensuse.org/developer.
 Ubuntu 10.04 LTS Beta 1 released
Ubuntu 10.04 LTS Beta 1 released
The Ubuntu team has announced the first beta release of Ubuntu 10.04
LTS (Long-Term Support) Desktop, Server, and Netbook editions and of
Ubuntu 10.04 Server for Ubuntu Enterprise Cloud (UEC) and Amazon's
EC2. Codenamed "Lucid Lynx", 10.04 LTS continues Ubuntu's open source
technologies into a high-quality, easy-to-use Linux distribution.
Ubuntu 10.04 LTS Desktop and Netbook Editions continue the trend of
ever-faster boot speeds, with improved startup times and a streamlined,
smoother boot experience.
Ubuntu 10.04 LTS Server Edition provides better integration of the
Ubuntu Enterprise Cloud, with its install-time cloud setup. Ubuntu 10.04
LTS Server for UEC and EC2 brings the stability of the Ubuntu Server
Edition to cloud computing, whether on Amazon EC2 or an internal Enterprise
Cloud.
Desktop features include built-in integration with Twitter, identi.ca,
Facebook, and other social networks with the MeMenu in the panel; new
notification area, new themes, new icons, and new wallpaper; Ubuntu
One Music store.
Please see http://www.ubuntu.com/testing/lucid/beta1/ for details.
Server features include the Ubuntu Enterprise Cloud installer with
support of alternative installation topologies (and is now powered by
Eucalyptus 1.6.2 codebase); official Ubuntu Server image releases for
UEC and for Amazon's EC2; improvements over Ubuntu 8.04 LTS in safety
and security for the next five years, including AppArmor profiles for
many key services, kernel hardening, and an easy-to-configure
firewall.
Ubuntu Netbook features include optimization to run on Intel atom
based netbooks; a new consumer-friendly interface that allows users to
get on-line and use their favourite applications; plus the same faster
boot times and improved boot experience as Ubuntu desktop.
Kubuntu 10.04 LTS will be the first LTS to feature KDE 4 Platform and
Applications. This release is focused on bug fixing and stability, but
adds features such as touchpad configuration, Firefox KDE integration,
Kubuntu notification improvements, and cross-desktop systray menu
standardisation. Kubuntu features the Plasma Desktop while Kubuntu
Netbook Remix comes out of preview status with the Plasma Netbook
workspace.
See https://wiki.kubuntu.org/LucidLynx/Beta1/Kubuntu/ for more details.
Mythbuntu 10.04 introduces MythTV 0.23. This new version is
significantly faster and should feel more responsive and stable than older
versions. It also integrates better into the OS.
Please see http://www.mythtv.org/wiki/Release_Notes_-_0.23/
for more details about changes introduced in 0.23. See http://mythbuntu.org/10.04/beta/
for information about the Mythbuntu beta release.
To upgrade to Ubuntu 10.04 LTS Beta 1 from Ubuntu 9.10 or Ubuntu 8.04
LTS, follow these instructions:
https://help.ubuntu.com/community/LucidUpgrades/.
Software and Product News
 Latest Oracle Lite Synchronizes with Open Source SQLite
Latest Oracle Lite Synchronizes with Open Source SQLite
With the new version of Oracle Database Lite, mobile users gain
continuous access to enterprise data even in the absence of a network
connection. New in this release of Oracle Database Lite is the ability
to bi-directionally synchronize data between the open source SQLite
database and the Oracle Database.
This release also provides centralized user and device provisioning
and management of SQLite-based mobile applications, allowing
disconnected users to have an experience virtually identical to users
who are connected.
Oracle Database Lite consists of Oracle Database Lite Client, a
small-footprint SQL database that runs on many devices and platforms and
can be bi-directionally synchronized with an Oracle Database server and
Oracle Database Lite Mobile Server, which enables mobile users and devices
to operate in occasionally connected environments, periodically
synchronizing with a back-end database server.
The Oracle Database Lite Mobile Server can also be used to provision
SQLite-based applications, devices on which these applications run,
and users of these applications. User authentication on client devices
can use a Common Access Card.
"Oracle Database Lite's Mobile Server is a great tool for data
synchronization in large scale enterprises," said Zdravko Mandic,
manager Research and Development, Infoart d.o.o. "Our implementation,
which consists of more than 1500 client devices, would have hardly
been possible without it. Oracle Database Lite works silently, in the
background, synchronizing huge amounts of data to our central Oracle
Database and vice versa. This automatic synchronization, combined with
great device management, is essential to keeping such large
deployments healthy and helps enable enterprises to stay up and
running all the time."
 Oracle Releases Updated Berkeley DB with Android Support
Oracle Releases Updated Berkeley DB with Android Support
Oracle has released Oracle Berkeley DB, the small-footprint, open
source embeddable database engine for mission-critical 'edge'
applications. This new version introduces a new SQL API, based on
SQLite, which is familiar to a large developer community and helps
simplify application development.
New features include support for JDBC and ODBC connections to Oracle
Berkeley DB. In addition, Oracle Berkeley DB 11g Release 2 introduces
support for the Android platform, allowing developers to develop and deploy
a wide range of applications on mobile devices.
Unlike traditional stand-alone databases, Berkeley DB runs directly in
the application that uses it, enabling applications to execute faster
in embedded environments such as handsets and mobile devices.
Key new features and benefits include:
- New SQL API;
- SQLite Tools Integration making it easier to develop, deploy, and
manage Berkeley DB applications;
- Flexible configuration including the library, cache size, database
location and transactions under the control of embedding application;
- Improved SQL concurrency using the Berkeley DB fine-grained locking
mechanism and write-ahead logging;
- Simplified Data Synchronization using the Oracle Database Lite
Mobile Server.
"Oracle Berkeley DB's new SQLite-compatible SQL API offers powerful
features for its users and the SQLite community at large. The
combination of the two technologies provides developers with
tremendous flexibility in that a single SQL/API can now be used across
a broad spectrum of applications. Oracle has done a fantastic job of
not only integrating the technologies, but also being an exemplary
participant in the open source community by contributing time,
expertise and resources to the SQLite project," said Mike Owens,
author of "The Definitive Guide to SQLite."
Oracle Berkeley DB 11g Release 2 was available for download on March
31, 2010.
 Red Hat Extends Its SOA Platform For Cloud Adoption
Red Hat Extends Its SOA Platform For Cloud Adoption
At EclipseCon in March, Red Hat announced JBoss Enterprise SOA
Platform 5.0, a major update to its JBoss Enterprise Middleware
portfolio. JBoss Enterprise SOA Platform 5.0 is an IDE that integrates
applications, services, transactions, and business process components
into an architecture for automating business and IT processes.
JBoss Enterprise SOA Platform 5.0 includes an updated enterprise
services bus with enhanced protocol listeners, Web services
integration, and a new rules engine that can be managed by JBoss
Enterprise BRMS (business rules management system).
Also expanding Red Hat's middleware portfolio is JBoss Developer
Studio 3.0. This platform now includes support for all of the JBoss
Enterprise Platforms; JBoss Enterprise Application Platform, SOA,
Portal and Data Services platforms. Additionally, the toolset is built
on the latest major release of Eclipse 3.5, and includes new
development capabilities for building SOA services and data
transformation tools for developing enhanced integration services.
To expand the use of cloud-based applications and services, the JBoss
Enterprise SOA Platform integrates applications and services in
cloud and on-premise deployments. Cloud-based IT has the potential to
further increase business process automation.
"Application development within the SOA-equipped enterprise has
evolved significantly over the past two years, demanding a more
eclectic and flexible arsenal of expertise and matching tools," said
Brad Shimmin, Principal Analyst Application Infrastructure at Current
Analysis. "Services and their underlying data must be considered
together, as do cloud and premise deployments, as do rich internet
applications and complex integrated services. JBoss Developer Studio
3.0 melds these disparate concerns using the agility of the Eclipse
3.5 platform and a broad quiver of supported frameworks that includes
RichFaces, Seam, Spring, Struts and GWT."
Red Hat featured both JBoss Enterprise SOA Platform 5.0 and JBoss at
Eclipsecon 2010 in Santa Clara, CA. For additional information on
JBoss Developer Studio 3.0 and to download an evaluation copy, visit
http://www.jboss.com/products/devstudio/.
Talkback: Discuss this article with The Answer Gang
![[BIO]](../gx/authors/dokopnik.jpg)
Deividson was born in União da Vitória, PR, Brazil, on
14/04/1984. He became interested in computing when he was still a kid,
and started to code when he was 12 years old. He is a graduate in
Information Systems and is finishing his specialization in Networks and
Web Development. He codes in several languages, including C/C++/C#, PHP,
Visual Basic, Object Pascal and others.
Deividson works in Porto União's Town Hall as a Computer
Technician, and specializes in Web and Desktop system development, and
Database/Network Maintenance.

Howard Dyckoff is a long term IT professional with primary experience at
Fortune 100 and 200 firms. Before his IT career, he worked for Aviation
Week and Space Technology magazine and before that used to edit SkyCom, a
newsletter for astronomers and rocketeers. He hails from the Republic of
Brooklyn [and Polytechnic Institute] and now, after several trips to
Himalayan mountain tops, resides in the SF Bay Area with a large book
collection and several pet rocks.
Howard maintains the Technology-Events blog at
blogspot.com from which he contributes the Events listing for Linux
Gazette. Visit the blog to preview some of the next month's NewsBytes
Events.
Magic and Mayhem
By Anonymous
It all started with SAK, the Secure Attention Key, that was supposed
to get me out of trouble in Ubuntu. The help I got was a kernel panic.
Investigations followed; doubts followed the investigations. I report
starting with a recap on SysRq, mainly from
http://www.kernel.org/doc/documentation/sysrq.txt
This doc lacks important information, but it is included here.
(1) What is the 'magic' SysRq key?
It is a key combo the kernel will immediately respond to, whatever it
is doing - assuming it was compiled with the CONFIG_MAGIC_SYSRQ
option. This is the case with the major GNU/Linux distros.
(2) Need the SysRq key be enabled?
No, when running a kernel with SysRq compiled in, the key is (usually) enabled.
However, distributions like openSUSE have a restricted value in /proc/sys/kernel/sysrq -
meaning that, according to their documentation, sysrq is disabled by default.
But you can disable or restrict it courtesy of /proc/sys/kernel/sysrq.
By default, this file contains 1 and SysRq is fully enabled (with some
exceptions - see above). To disable SysRq, write 0 to the file.
To restrict functionality selectively, pick values from this table:
| Value | Option |
| 2 | Enable control of console logging level |
| 4 | Enable control of keyboard (e.g. SAK) |
| 8 | Enable debugging dumps of processes etc. |
| 16 | Enable sync command |
| 32 | Enable remount read-only |
| 64 | Enable signalling of processes (term, kill, oom-kill) |
| 128 | Allow reboot/poweroff |
| 256 | Allow rescheduling |
Pick your options, sum their values, write the sum to
/proc/sys/kernel/sysrq; after that, only your options will be
allowed.
The value in /proc/sys/kernel/sysrq determines the shortcuts available
to all users and is not subject to permissions. However, writing to this
file requires root privileges. And since the file is not really a file
and dies when shutting down or rebooting, the writing has to be
repeated after each boot.
The option 'sysrq_always_enabled' in the kernel line of the boot
loader will let the kernel ignore /proc/sys/kernel/sysrq.
(3) How do I use the SysRq key on x86 PCs?
Press the key combo Alt-SysRq-command_key, where 'SysRq' is
same as 'PrintScreen' and command_key is a case-insensitive
letter or a digit from
b,c,d,e,f,g,h,i,j,k,l,m,n,o,p,q,r,s,t,u,v,w,x,z,0-9
Needless to say, it is awkward or even infeasible to hold down three
keys at once when two of them are a stretched hand apart. Just do:
hold down Alt (either on the right or on the left)
press and release SysRq quickly
press command_key quickly
release everything
Quickly means: don't dither, or Ubuntu will pop up a Screen Shot dialog.
NOTE: the position of keys is as on the US keyboard! Keep this in mind when
using a non-US keyboard. For instance, 'q' is the key just right of
Tab even if that same key carries the label 'a' on a French keyboard.
Indeed, you are not sending an 'a' or a 'q': you are sending a well-defined
scancode to the kernel. Keyboards needn't apply if they produce scancodes
different from those of the common PC keyboards.
Only details for a couple of the commands are of interest in the
current context:
| i | Kill all processes, except init. |
| k | Secure Attention Key (SAK) kills all applications on the
current virtual console. |
| 0-9 | Sets the console log level, controlling which kernel messages will show on your console: 0 would let only emergency messages reach the console while 9 is verbose. |
(4) Kernel Panic
So why do I very reliably trigger a kernel panic when I press SAK on
Ubuntu 9.10, both in the text console and on the desktop? The
difference between the two is that the kernel panic is immediate in
the text console. On the desktop it may look like everything is ok,
then you press e.g. Alt-Ctrl-F1 to switch to a text console and it
happens.
Well, this is a bug already reported in February 2009 for a previous
version:
https://bugs.launchpad.net/Ubuntu/+source/linux/+bug/329576/
An addendum to the bug report says the bug manifests on AMD boards, but
not necessarily on Intel boards. I can confirm that I do get my kernel
panic on AMD hardware, but I have also seen it on an Intel motherboard
with a VIA graphic adapter.
A related bug was reported for Debian in August 2009:
http://bugs.debian.org/cgi-bin/bugreport.cgi?bug=543324/
but here the console-kit-daemon was pointed out as the culprit. I
disabled it, the bug is still active on my Ubuntu.
Changing the log level with Alt-SysRq-9 allows for a flood of
low level details for the initiated. What is clear, reading and watching,
is that an attempt to kill the 'init' process occurs - certainly not the
kernel's intention. Who is trying to kill init? Something specific to
Ubuntu, shall we say, since openSUSE doesn't do it.
Now, when I try Alt-SysRq-i to kill all processes except init,
I get a kernel panic exactly as with SAK, exactly with the same message
about init's attempted murder.
That Ubuntu bug of February 2009 got no follow-up, not even an assignment
to a developer, not even a priority rank. What does it take for serious
bugs to get fixed in Ubuntu?
(5) Security by Good Luck
At the end of the day, what we know is disturbing:
- Everybody wants the magic of SysRq, otherwise the major distros
would not compile it in.
- The administrator can reduce SysRq's functionality, but not just
for the unwashed masses. Any reduction in SysRq's functionality
will equally affect the administrator. Functionality cannot be
changed on the fly, because when a critical situation arises you
already need it.
- Even disregarding bugs like Ubuntu SAK's bug, SysRq has options to
bring down and damage the entire system. If you start disabling
them, SysRq loses its magic in the difficult situations it is
called for. So if you as an administrator want SysRq, you are
offering vandals and experimenters a comfortable way to wreak
havoc.
Is a GNU/Linux system the most insecure system in the history of
computers? Why is the SysRq magic not reserved for root?[1]
[1]
That's an easy question to answer - although, unfortunately, the answer
does nothing to address this concern. Since most Linux users are
(hopefully) not logged in as root most of the time, restricting SysRq to
root-only would make it essentially useless at precisely the times when
it's needed. Perhaps a reasonable approach to a SysRq policy is to disable
the "dangerous" features by default, and enable them on specific machines
that need more specific troubleshooting?
-- Ben
Talkback: Discuss this article with The Answer Gang
 A. N. Onymous has been writing for LG since the early days - generally by
sneaking in at night and leaving a variety of articles on the Editor's
desk. A man (woman?) of mystery, claiming no credit and hiding in
darkness... probably something to do with large amounts of treasure in an
ancient Mayan temple, and a beautiful dark-eyed woman with a snake tattoo
winding down from her left hip. Or maybe A.N. is just into privacy. In
any case, we're grateful for the contributions.
A. N. Onymous has been writing for LG since the early days - generally by
sneaking in at night and leaving a variety of articles on the Editor's
desk. A man (woman?) of mystery, claiming no credit and hiding in
darkness... probably something to do with large amounts of treasure in an
ancient Mayan temple, and a beautiful dark-eyed woman with a snake tattoo
winding down from her left hip. Or maybe A.N. is just into privacy. In
any case, we're grateful for the contributions.
-- Editor, Linux Gazette
Copyright © 2010, Anonymous. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
Linux's problem with Simplified Chinese
By Silas Brown
Chinese characters are used not only in Mainland China but
also in Taiwan, Hong Kong, Japan, and sometimes in Korea and
other places. There are differences in the way these
countries write certain characters, and ideally this should
just be a matter of selecting a different font. However, for
various reasons some (but not all) of the "Simplified
Chinese" characters used on the mainland have been given
their own Unicode numbers that are different from the Unicode
numbers of their nearest equivalent characters in Japan, etc.
This leads to a problem.
Imagine a typical text in Simplified Chinese. Some of the
characters have their own special code numbers that occur
only in Simplified texts, whereas other characters have code
numbers that can also occur in Japanese and other texts. Now
imagine that a rendering system such as Pango is going to
render this text. Pango takes the text character by
character, and tries to find each character in the available
fonts. Suppose it first of all finds a character that occurs
in a Japanese font. There is a Japanese font on the system,
so it takes that character from the Japanese font and renders
it. But then the next character is not in the Japanese font
because it is a special Simplified character that occurs only
in a Simplified Chinese font. There is a Simplified
Chinese font on the system too, so off it goes and renders
that second character from the Simplified Chinese font.
The problem is that some of the characters (the ones that
have special Simplified-only codepoints) will be rendered
from the Simplified Chinese font, but others (the ones that
share codepoints with Japanese etc) will be rendered from
another font. If the fonts happen to have the exact same
style and weight, etc., then nobody will notice, but usually
there are noticeable differences in style between the fonts,
so this mixing of fonts, with some characters taken from one
font and others taken from another, can make the display of
Simplified Chinese on Linux look very unprofessional.
Many users can tolerate this situation on the screen, but
printing is a different matter. For example, the music
typesetting system GNU Lilypond uses Pango to render the text
of lyrics, etc., and if you want to produce beautiful-looking
copy with Simplified Chinese text, this
character-by-character mixing of fonts could be a
showstopper.
The Pango renderer does have facilities for application
programmers to specify the language and therefore influence
the choice of fonts, such as by calling
pango_context_set_language() or by using Pango markup.
However, this is small consolation for those using
applications that do not expose this functionality to the
user.
One thing you can do is edit your ~/.fonts.conf
file to tell the system which fonts you prefer. This will
affect all applications, so you may need to change it back
when you want to see Traditional Chinese or Japanese, etc.
Below is a ~/.fonts.conf file which specifies the
Arphic Simplified Chinese font as a preference (Debian/Ubuntu
package ttf-arphic-gbsn00lp). It also specifies
DejaVu for the Latin fonts, along with Gandhari, a font which
is good for Pinyin markup.
<fontconfig>
<alias>
<family>serif</family>
<prefer>
<family>gandhari unicode</family>
<family>dejavu serif</family>
<family>ar pl sungtil gb</family>
</prefer>
</alias>
<alias>
<family>sans-serif</family>
<prefer>
<family>gandhari unicode</family>
<family>dejavu sans</family>
<family>ar pl sungtil gb</family>
</prefer>
</alias>
<alias>
<family>monospace</family>
<prefer>
<family>dejavu sans mono</family>
<family>ar pl sungtil gb</family>
</prefer>
</alias>
</fontconfig>
On a Debian or Ubuntu system, most of the families can be
seen by looking at
/var/lib/defoma/x-ttcidfont-conf.d/dirs/TrueType/fonts.dir.
To install Gandhari, download it from Andrew Glass's
site, visit fonts:/ in Konqueror (package
konqueror if you don't already have KDE) and drag
gur.ttf into that folder.
This approach does not solve everything; for example, the
on-screen display of Chinese in Tk applications might still
be inconsistent (it does not seem possible to set a preferred
order of fonts in Tk/X11; you can set one
preferred font but there's no obvious way to control what it
falls back on when displaying characters that are not
available in that font). However, the use of ~/.fonts.conf
should at least help with applications that you are likely to
use for printing.
Talkback: Discuss this article with The Answer Gang
![[BIO]](../gx/authors/brownss.jpg) Silas Brown is a legally blind computer scientist based in Cambridge UK.
He has been using heavily-customised versions of Debian Linux since
1999.
Silas Brown is a legally blind computer scientist based in Cambridge UK.
He has been using heavily-customised versions of Debian Linux since
1999.
Copyright © 2010, Silas Brown. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
Away Mission - Recommended for April
By Howard Dyckoff
Spring has sprung and the venerable MySQL User Conference is coming up. That
conference is still independent of the Oracle OpenWorld behemoth, partly
due to the promises Oracle made to the EU about keeping MySQL alive and
independent. But don't blink: the separate focus on the respected Open Source
database may not last. So do drop in to see the event and its expo if you
have a chance. Expo passes may still be free in early April.
MySQL Conference & Expo 2010
April 12-15, Convention Center, Santa Clara, CA
http://en.oreilly.com/mysql2010/
I would also recommend the Linux Foundation's 4th Annual Collaboration
Summit - if you can wangle an invite. It is a gathering place for kernel
developers and Open Source rock stars, but the sessions are detailed and
real collaboration occurs.
The Summit does overlap the MySQL event by 2 days, but it should be
possible to catch the opening MySQL keynotes and then attend the Summit for
the rest of the week. I would have to rate the food and snacks a bit
better at the O'Reilly-run MySQL Conference, and in both cases the company
is stellar. At the Summit this would include core kernel developers,
distribution maintainers, ISVs, end users, system vendors, and other
community organizations. It's geared to collaboration and solutions by
bringing together a cross-section of leaders to tackle and solve the most
pressing issues facing Linux today.
Attendees of the CELF Embedded Linux Conference and the LSF '09 Workshop
will be automatically approved. Or, just enroll in the LF324 Linux Performance
Tuning Linux Training Course and get a free invitation to the Linux
Foundation Collaboration Summit.
Here's the location for the slides from last year's Collaboration Summit:
http://events.linuxfoundation.org/archive/2009/collaboration-summit/slides
Linux Foundation Collaboration Summit
co-located with the Linux Forum Embedded Linux Conference
April 14-16, 2010, Hotel Kabuki, San Francisco, CA
Finally, I also have to recommend the excellent Emerging Communications
Conference, which returns the the San Francisco Airport Marriott again. It
has been a cross between a Maker event, an Open Source network event, and
something entirely its own.
Slides from the previous event are here: http://www.slideshare.net/ecommconf
eComm - The Emerging Communications Conference
April 19-21, 2010, Airport Marriott, San Francisco, CA
http://america.ecomm.ec/2010/
Talkback: Discuss this article with The Answer Gang

Howard Dyckoff is a long term IT professional with primary experience at
Fortune 100 and 200 firms. Before his IT career, he worked for Aviation
Week and Space Technology magazine and before that used to edit SkyCom, a
newsletter for astronomers and rocketeers. He hails from the Republic of
Brooklyn [and Polytechnic Institute] and now, after several trips to
Himalayan mountain tops, resides in the SF Bay Area with a large book
collection and several pet rocks.
Howard maintains the Technology-Events blog at
blogspot.com from which he contributes the Events listing for Linux
Gazette. Visit the blog to preview some of the next month's NewsBytes
Events.
Copyright © 2010, Howard Dyckoff. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
Pixie Chronicles: Part 1 Lessons from Mistakes
By Henry Grebler
Adam
I had a friend, Adam, who passed away far too young. Adam seemed to be
competent at an amazing number of activities, mostly self-taught. He
built himself a house almost single-handedly.
He once shared with me the secret of building. Adam would say that it
was not possible to build a house without making mistakes. The secret,
he said, was hiding your mistakes. For example, builders can never get
the floor and walls to fit together exactly. So they invented skirting
boards; for walls and ceiling: mouldings and cornices.
Subsequently, somebody must have decided to extend the concept and
they became decorative. Now that's really hiding your mistakes -
pretend that they are a feature!
Perhaps because I know (or think I know) more than the average bear
about Linux, I get "adventurous", particularly on my projects at home.
When I extend my activities beyond my areas of competence I frequently
make mistakes. That's not intrinsically a bad thing: you have to break
eggs to make an omelette. But it's important to be able to recover
from mistakes.
As a result, I've adapted Adam's advice to fields which interest me.
Project
My project for last week was to build a server. Sounds simple. What
could possibly go wrong? Watch and learn.
I run (the fairly old) Fedora Core 5 on my desktop, so I thought I'd
install the latest Fedora on my server. I say "server" but it's
actually a Pentium II, one of a pair a friend was throwing out. The
other one replaced my aging (12-year-old Pentium 1 100) firewall.
But my project is more about concept than commercial-strength mail and
web-serving, so grunt[1] is not important to me.
Installing from CDs holds no fascination for me: I've done it so many
times, the novelty has worn off. I decided I'd do a "Look, Ma! No
hands!" install.
The Pentium II was a Compaq which must have been quite leading edge
when it was purchased. Of particular interest was the fact that it had
on-board hardware PXE capability. I conceived a plan which would see
the machine perform a network boot, then perform a network
install driven by a kickstart file. Everything would be
automatic: partitioning, timezone, system language, configuration of 2
NICs, root password - the lot.
As an exercise in building a single server, this approach is not very
efficient. However, as an exercise in building multiple servers, it is
excellent. One of the dangers of having a human (me) perform the same
task repeatedly is that boredom sets in and the human (me) loses
concentration, leading to mistakes. It is worth investing effort into
automating the process. Although I currently have neither the hardware
nor the need to build a farm of servers, I would like to learn the
technique for the future. So for me, this is a learning exercise.
The following sections are written from the perspective of the machine
to be built, which I'll call the target machine.
Typical Install
To provide some context, here is an overview of a typical
install. Bear in mind that my old Compaq only has a CD drive (not
DVD).
- Turn on the target machine.
- Insert the first install CD.
- Machine boots from the removable disk, loading the install environment.
- Proceed through many screens answering questions about partitioning, timezone, system language, etc.
- The machine begins to install from the first CD.
- After a while, the machine asks for the second CD.
- Change CDs.
- Repeat until all 6 install CDs have been processed.
Note that the numbered steps involve human intervention. The indented
sentences describe the target machine's behaviour.
Intended Install
Here is my rough plan for how things were supposed to go.
- Turn on the target machine.
- Machine starts the boot process, asks the network for an IP
address, then downloads the install environment.
- The install environment uses the kickstart file to guide
the rest of the install. It obtains the install
files from the network. No further intervention is required.
Actual First Attempt
And here's what happened the first time.
- I turned on the target machine.
- The machine booted, asked the network for an IP address, then
downloaded the install environment.
- The install environment used the kickstart file to guide
the rest of the install.
However, it was here that I discovered the first of several mistakes.
I had not defined the partitioning information completely, so the
machine stopped to ask for clarification.
I guess I could have gone back and fixed the problem and restarted,
but it occurred to me that I might have made other mistakes. I decided
to answer the partitioning questions and proceed.
Remarkably, that was the only problem. Or so it seemed. The
install proceeded. It seemed to take a very long time, but I was
not too surprised by this: the target machine is, after all, a Pentium II.
It is at this stage that a kickstart install starts to pay back. The
install may take a long time, but I don't have to stay around to
change CDs. There are always other tasks to be done, and in this case
I left the room for several hours.
On my return, the machine was again asking for clarification about
partitioning!
What had happened?!
Things Go Wrong
There is a temptation when things go wrong to start doing. This
is almost invariably bad. It often leads to regretting!
It takes some discipline and experience to stop and think.
"Doing" quite often leads to activities which modify the "crime scene".
One then gets to a point where one wants to know what something looked
like before the "doing" began. Too late.
"Thinking" doesn't prevent all mistakes, only some.
What had gone wrong?
How does one even begin to think in such a case? Well, every activity
typically has a beginning, a middle, and an end.
The install had started ok. I'd then had the partitioning
problem. After that, the install seemed to proceed as expected.
So beginning and middle seemed to be off the hook. I concluded that I
should look at the end.
What should have happened after the install completed?
I remembered that one of the kickstart parameters related to this.
I had requested that the machine reboot after install.
In an install from CD, once the install environment has processed
the last CD, it asks the user to remove any install media from
the drive. By default, when the machine subsequently reboots, it takes
its data from the recently installed hard drive.
However, in my case, on reboot, the machine performed its PXE boot -
which restarted the install process. Thank heavens for my
partitioning mistake. Without it, the install would have
proceeded as before, come to the end - and started all over again. It
might still be at it now, repeatedly booting and installing!
I guess after a few days I might have grown suspicious.
It's an ill wind that blows no good; and sometimes, as in this case, a
mistake can be your friend.
Analysis
My first mistake was unexceptional. To install FC10 I needed to get a
number of steps right. As we shall soon see, I've glossed over some of
the steps to tell this part of the story simply. It is unsurprising
that I did not get everything right the first time. (I would have been
very surprised had everything just worked!)
The second mistake was much more interesting. It relates to the case
where an action is repeated but the conditions change between the
first and a later occurrence of that action. It's the sort of problem
that is common in loops.
In this case, the first time I booted the machine, I wanted it to use
PXE; the second time, I didn't. I hadn't realised that I had wanted
different behaviours.
Even stated like this, it was not clear to me what to do next. At
first sight, the simple solution is to request that the install
environment not reboot at the end of the install. But, as we
shall see in the next part, that solution is somewhat short-sighted.
Lessons
When something goes wrong, don't rush to act. Stop, think, and plan
before acting.
[1]
Reading Henry's articles is giving me a great workout in Aussie
colloquialisms - "grunt" in this case, I'm told, means "muscle", i.e.
computing power. -- Kat
Talkback: Discuss this article with The Answer Gang
![[BIO]](../gx/authors/grebler.jpg)
Henry was born in Germany in 1946, migrating to Australia in 1950. In
his childhood, he taught himself to take apart the family radio and put
it back together again - with very few parts left over.
After ignominiously flunking out of Medicine (best result: a sup in
Biochemistry - which he flunked), he switched to Computation, the name
given to the nascent field which would become Computer Science. His
early computer experience includes relics such as punch cards, paper
tape and mag tape.
He has spent his days working with computers, mostly for computer
manufacturers or software developers. It is his darkest secret that he
has been paid to do the sorts of things he would have paid money to be
allowed to do. Just don't tell any of his employers.
He has used Linux as his personal home desktop since the family got its
first PC in 1996. Back then, when the family shared the one PC, it was a
dual-boot Windows/Slackware setup. Now that each member has his/her own
computer, Henry somehow survives in a purely Linux world.
He lives in a suburb of Melbourne, Australia.
Copyright © 2010, Henry Grebler. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
Yes, Master
By Henry Grebler
Dogs are the leaders of the planet. If you see two life
forms, one of them's making a poop, the other one's
carrying it for him, who would you assume is in charge?
- Jerry Seinfeld
I'm not in the habit of bagging Microsoft. No, really. Oh, all right,
I am.
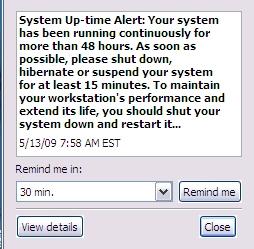 Have a look at this picture. I swear that it's for real. It popped up
on more than one occasion on my company laptop. I don't know
whether it came from XP, some other piece of Microsoft software, or
some other software altogether. But it just beggars belief!
Have a look at this picture. I swear that it's for real. It popped up
on more than one occasion on my company laptop. I don't know
whether it came from XP, some other piece of Microsoft software, or
some other software altogether. But it just beggars belief!
I just looked on my Linux desktop: uptime - 126 days. I don't even
think that's a particularly impressive number.
All right, my desktop is not a laptop. So?!
And what is it with turning it off for at least 15 minutes? Nap time?!
Imagine if they used this technology in, oh, fridges! Ships! Rockets
to the moon! Military equipment! I'm sorry. Your war is important to
us. To maintain your military lethality and extend its life, please
shut down your war for at least 15 minutes.
Monday
OK, I've arrived at the office. 7:45 am. Nice and early. Good. I'm a
morning person. It's great to come in before most of the others get
in. Gives me time to do some work that requires concentration before
the distraction level ramps up.
Wonder why they put us into these open-plan areas. Do they really
think they are saving money? Or is it to do with pecking order?
They're paying me a shirt-load of money, and yet I can hear the guy way
over there on the phone to one of his customers. Try to concentrate.
Crumbs, he's loud! They used to call me loud, but now I'm in the
presence of a real master.
Get out the laptop. Turn it on. Get some real work done. Come on, boot
up already! First password. Second password. Come on, XP! Finally:
login password. What's it doing?
What's this? Virus scanner. Updating signatures. No response for me.
Come on!
Why did I turn on this #@$#&^ing computer? Who's the human? WTF is
going on here?
What now? Some of my software is out of date. I don't even use that
software. Why would I care if it is out of date? I just wanna do some
work, for crissake! Who's in charge here?
Start up Adobe. Wait for it to update something. This is crazy!
There seems to be this view that I'm the laptop's lackey. I'm here to
service its requirements. It gives the orders; I follow. Its needs are
more important; mine are secondary.
Are we for real? The lunatics are in charge of the asylum!
A better way
Are we saying that we have reached the pinnacle of technical
engineering? That this is the best we can do?
Well, we know that there are various forms of improvement. On my Linux
systems, I run no regular antivirus software. Or antispyware. Or any
other sort of anti-malware software. (The only reason I have
any antivirus software at all is so that I can scan my teenage
son's Microsoft computer.)
The argument is that if Linux were as ubiquitous as Microsoft, then
the malware generators would attack Linux. As it is, they're just after
the low-hanging fruit.
All right. Let's accept that. For the sake of argument, let's
assume that it is necessary to update things on a Microsoft PC.
Fine. Can't we do that in a less obnoxious way?
Let's start with some low-hanging fruit of our own.
Sometimes, I reboot my computer repeatedly in a short space of time.
(Never mind why; it can happen.) Is it really asking too much of the
cretinous antivirus software to keep track of when it was last invoked
(or when I last rebooted), and to not even run if less than X hours
have elapsed?! And, OK, if some user actually wants every one of the
three reboots in the last hour to be followed by a scan, let him/her
configure the software to do that. Hell, I don't even mind if it's the
default. Just give me the option to do what I want.
That's what's really missing from a lot of software which runs on
Microsoft platforms: user choice. The technology which should be the
most liberating has been engineered to be antidemocratic. And
down-right irritating.
OK. There are times during the day when I get up from my seat and walk
away from my desk. Corporation rules say that I'm supposed to
screenlock the laptop when I leave. Even if I don't, after a few
minutes, the laptop does it anyway. Hey, you now know that I'm
not at the computer. You know I'm not pressing keys. Wouldn't
you think that now would be a good time to use up CPU cycles? I
don't need them. I've gone off to make myself a coffee and discuss the
weekend's footy with Alex.
I come back to the computer, enter my password. Don't abort what you
were doing; pause it. You are a machine of infinite patience. (Or
software of infinite patience.) Make a little note somewhere of where
you were up to - and take a break. When I wander off next time,
continue from where you left off.
Eventually, I head off for lunch. Hey, knock yourself out. Scan all the
hard drives. As far as I care, make the whole machine walk across the
desk from the vibrations. Do whatever you need to do. Just make sure
you pause when I come back.
I'm at work for about 8 hours. Despite the little pop-up I showed before, I often turn on the laptop on
Monday morning and don't turn it off again until Friday evening. In 24
hours, I only use 8-10 hours. You can have a minimum of 14 hours to do
whatever you want. Just not on my watch.
What am I missing?
Is this so hard?
Is it beyond the capabilities of the mind of Homo Sapiens?
Perhaps it would not be possible 100% of the time. Sometimes, perhaps,
something might need to be updated urgently. Personally, I think this
most unlikely - but I entertain the possibility. But even if we can
only arrange things so that I am undisturbed 90% of the time, that's
still a huge improvement over what I see currently.
You can not be serious!
[
Pace, John McEnroe.]
What is it with Microsoft and reboots?! Look at this:
OK, it's a joke, a reductio ad absurdum of the state of play at
Microsoft. Compare that to BeOS which was designed to never need
rebooting. Perhaps it's asking a bit too much of Microsoft to
never need rebooting.
But why does it need to reboot if I change my IP address? Or a host
of other fairly innocuous changes I make to the system?
All day long, I am bombarded with stupid questions: Are you sure? Did
you really mean that? Is it OK to reboot now? Do you want fries with
that? No, wait, that last one was from some other company.
Now here's an idea: how about, when I ask to shutdown or reboot, I get a
prompt? Wouldn't that be a perfect time to say something like this?
X
Hey! All day long I've been nagging you to upgrade your software, all the
while discouraging you with threats that such upgrades will almost
certainly necessitate a reboot (which I call a "restart" because God forbid
we should spook the bunnies who use our, um, software with technical
terms). Well, I notice that you're about to shutdown or restart. Is now a
good time to do those upgrades? I mean, do you have the time? (If you're
heading home, you could take a pit-stop.)
If now is not convenient, that's OK. I'll remind you next time.
OK Cancel
First of all, isn't that a good idea? And second, just maybe, isn't
that a more appropriate tone for a pile of silicon to adopt
when addressing a superior life-form?
Perhaps I shouldn't be surprised. I've always thought that Microsoft
treats its users with contempt. Surely the tone it adopts in its
dialogues and messages supports that view. The smug little utterances
like "Windows must shutdown your computer now". The higher power has
spoken!
Of course, once it has completed the upgrade, when it's time for the,
ahem, restart, it will take cognizance of my original selection. In
particular, if I chose to shutdown, it will, at this time, shutdown.
When next I fire up my machine, it will proceed with any subsequent
actions needed to complete the install. The idea is to maximise
utility and convenience for me. Because I'm the human.
It's not about you; it's about me.
Scanning for Pleasure
Turn on wife's machine. Windows 98. What's this? Disk scan? Scan disk?
What is it doing? Just another way to slow me down.
In fairness, I should say that I haven't seen this on XP. But on my
wife's Windows 98, it is very frequent.
I speculate that one day, quite some time ago, Bill was walking past a
machine when it was booting into Linux. It was just at the point where
it was doing an fsck.
"What's happening?" he asked.
The Linux user explained it to him.
Later, Bill summoned his Council of Technical Acolytes.
"Linux does something called fsck when it starts up. I want
something like that for our next release of Windows."
"But, Sire," offered one of his Council. "We don't need to do that.
Our software works differently."
"Nonsense!" snapped Bill. "If Linux has it, we need a competitive
story. We can't be open to criticism that we lack technical rigour.
"Further, we need it for another reason. It's important that our users
get into the habit of obeying, preferably without thinking. If they
ever get to thinking about our offering, well, ..." He trailed off,
shaking his head to discard the unthinkable.
"OK, gentlemen. Take notes. Here's how it's going to work. We will
insist that they shutdown their machines in a certain way. It's
important that they learn to follow orders. We'll detect if they
obeyed. If they did, fine. The plan is working.
"If not, we'll use this - what did he call it? fsck? Stupid
name - we'll use our version of fsck to punish the user."
Sensing resistance, he glared at the members of his Council. One or
two, whose hands had been up, lowered them.
"Excellent! Now let's get down to the most important part of this
exercise. fsck is such a stupid name. And anyway it's used by
the competition. So what will we call it?"
Bill looked up encouragingly. It looked like he was really asking for
suggestions. Several names were bandied around. Bill's countenance darkened.
"You don't seem to be getting it. None of your suggestions reach out
to me. I guess I have to do everything myself. Now let me think ..."
The buzz of conversation died down as the The Great One cogitated, the
silence broken only by an almost imperceptible sound, like gears
grinding.
"I've got it!" he cried out in satisfaction. "SCANDISK."
He looked triumphantly around the Council Chamber.
"But, Sire, don't we already have something called DISKSCAN?"
"That's not the same thing at all!" snapped Bill. "Hands up anyone who
thinks SCANDISK is like, um, DISKSCAN."
It doesn't actually do anything - unless you call moving the progress
bar doing something. It's just there to punish recalcitrance.
And the ultimate irony? Soon afterwards, Linux adopted a journaled
file system, eliminating the need to check the file system even after
an unclean shutdown.
You're probably thinking to yourself that my wife and I get what we
deserve. I'd agree with you about me; but my wife is what is so coyly
referred to as collateral damage.
Do you want to know why we have to run SCANDISK all the time? Because
Windows lies to us.
My wife finishes her work. She shuts down as prescribed - by clicking
on Start (!) and then following the bouncing ball. Eventually a splash
screen appears.
Windows is shutting down
She waits. She does other things. It's time for bed, so she performs
her nightly ablutions. She likes to read before going to sleep. You're
not really interested in my wife's nightly routine.
Hours later, the stupid machine still hasn't turned off. She calls me
to investigate. I look at her screen.
Windows is shutting down
Bill's message looks back at me mockingly. How much can a koala bear?
Enraged, I turn off the power at the wall.
Next time her machine is powered up, Bill gets his revenge. D'oh!
Talkback: Discuss this article with The Answer Gang
![[BIO]](../gx/authors/grebler.jpg)
Henry was born in Germany in 1946, migrating to Australia in 1950. In
his childhood, he taught himself to take apart the family radio and put
it back together again - with very few parts left over.
After ignominiously flunking out of Medicine (best result: a sup in
Biochemistry - which he flunked), he switched to Computation, the name
given to the nascent field which would become Computer Science. His
early computer experience includes relics such as punch cards, paper
tape and mag tape.
He has spent his days working with computers, mostly for computer
manufacturers or software developers. It is his darkest secret that he
has been paid to do the sorts of things he would have paid money to be
allowed to do. Just don't tell any of his employers.
He has used Linux as his personal home desktop since the family got its
first PC in 1996. Back then, when the family shared the one PC, it was a
dual-boot Windows/Slackware setup. Now that each member has his/her own
computer, Henry somehow survives in a purely Linux world.
He lives in a suburb of Melbourne, Australia.
Copyright © 2010, Henry Grebler. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
Codeweavers vs. Cedega, Commercial Wine Product Comparison
By Jeff Hoogland
Most people who use Linux for desktop use are well aware of the one of
the largest issues facing the platform: Lack of commercial software. Now in
most cases this is not an issue, no MS Office - use OpenOffice, no Internet
Explorer - use FireFox. However one thing which there is currently no
replacement for is gaming. Try as they might there are just not enough
Open-Source game developers (or even closed-sourced ones) that bring the
level of gaming quality, as of yet, to Linux that Windows enjoys.
Enter the world of Win-on-Lin. The Wine Project, was started in 1993 and
has slowly come into maturity over the course of the last sixteen years.
Wine is a compatibility layer, or more precisely a reimplementation of the
Windows API, that allows Windows applications to run under Linux. While the
Wine project does a wonderful job of what it is designed to do (run Windows
applications on Linux) how ever it sorely lacks in the means of a GUI front
end for easy configuration/calibration.
Which brings me to my topic at hand - Cedega & Codeweavers. What are
Cedega and Codeweavers? They two (closed source) programs both based off of
the Wine Project to create what it lacks - a user friendly interface.
Designed to help you get your Windows games working with ease on Linux.
They both have their ups and downs and today I am going to look at each
program and see how they compare. I currently have both Cedega and
Codeweavers licenses so all the information given is from first hand
experience working with both products. I'm going to be judging based on
following criteria:
- Functionality - How well do they do what they are
suppose to do?
- GUI Front End - How do the front-ends between the two
compare?
- Website - Being able to find information is
everything, how do the websites compare?
- Customer Service/Support - If you are paying for a
product you want to know you can get help with it if it doesn't work
properly.
- Fees & Licensing - How much do they cost and what
are you paying for?
Functionality
Cedega does a fairly good job of helping the user get their programs up
and running. Upon selecting install it auto-detects any disc drives on the
system for known game discs it can install. If it does not find any (or
finds the wrong one) it is easy enough to direct it to the proper file/disc
via the GUI. One of the things I really like about Cedega is the large
number of pre-defined profiles it contains for different game titles (and
just because you game isn't listed doesn't mean it will not work).
Basically what this means is when you install a game that has a profile it
automatically uses what are known to be the "best Wine settings" to get the
optimum performance out of your game.
While Cedega does a great job at actually running the important parts of
your games it is obvious that certain aspects of some programs have been
neglected, Steam for instance works fine for loading and playing games but
the friends network does not work in the slightest and installing flash for
it is difficult at best.
Also worth noting here is that while Cedega started off as a fork of the
Wine project (version 4.0 and earlier of Cedega was known as WineX or Wine
Extreme) initially, it is no longer associated with it. Because of this of
this fact the Windows API behind Cedega is also now different from that
which powers Wine and as such there are a few applications that will not
function under Wine (or things powered by Wine) that perform with out a
hick-up under Cedega.
All in all I'm giving Cedega a 9 out of 10 points for functionality - it
is a good software.
Functionality 9/10 - Cedega Total 9/10
Upon opening the Codeweavers program installer you are presented with a
small list of applications that it will auto install and configure for you.
I say small list because by comparison to the amount of game profiles
listed under Cedega it feels somewhat incomplete. How ever as with Cedega
just because the game you want to run is not on the list does not mean that
it will not work. Also like Cedega, Codeweavers will auto detect any disc
drives you have when you go to install a piece of software, one thing I
also really like is that when detecting disc drives it also detects mounted
iso files you may want to install from.
While the given list of games that are pre-configured in Codeweavers is
small compared to the games list present in Cedega, it is very obvious that
most of the games on the list have been worked on extensively to get them
working to a optimum level with a careful attention to detail. Using Steam
as my example again upon installation Codeweavers downloads and configures
flash, in addition to other things, to help it work almost as good as it
does natively on Windows (the only issue currently with the Steam UI is a
small scroll bar issue).
Codeweavers is based directly off the Wine project, as such if a program
works poorly under Wine odds are it is going to work just as poorly under
Codeweavers. As such this also means that any performance you see with an
application under Codeweavers can be replicated under just a standard Wine
install (how ever it may take you several hours to get everything just
right).
I'm giving Codeweavers an 8 out of 10 on functionality. It is good
software but it needs to expand its games list some.
Functionality 8/10 - Codeweavers Total 8/10
GUI Front End
One of the most important things about both these pieces of software is
their GUI. One of the wonderful things about Linux is how alot of things
"just work" and having a front end to install Windows applications through
is a nice addition to have.
The Cedega GUI does a nice job of giving you a centralized location to
house all of your Games/Windows applications. (You can add launchers for
your favorite native Linux apps/games to it as well) Also present in Cedega
that Codeweavers does not have is a "diagnostic test". Basically it checks
over your hardware and configuration for anything that may cause issues
when running your games. In addition to being able to check your
configuration the diagnostic tool also allows for an easy copy and paste of
your system specifications which is useful if you are unsure of your setup
(or too lazy to type it out) when trying to debug an issue.
Lacking in the Cedega GUI how ever are native menu entries. Applications
installed under Cedega often times feel foreign as you have to open a
separate program to launch them or create your own custom menu entry (and
hunting down the correct icon for you game can be a headache). Also worth
noting with netbooks becoming more and more popular is that the Cedega GUI
is obviously designed for a resolution of at least 768 pixel height, parts
of it get cut off on most netbook screens. The Cedega GUI as a whole is
good but it could stand a few changes - 8 out of 10
GUI Front End 8/10 - Cedega Total 8.5/10
While Codeweavers does not give you a centralized location for all your
install applications like Cedega does, however it is still well done.
Codeweavers does a beautiful job of integrating with your local menus
(Gnome, KDE, ect) when installing applications. In fact if Codeweavers
would simply add the games you install to the games section of your menu
instead of its own section I do not think most users would be able to tell
the difference between a natively installed game and one installed via
Codeweavers. Same as Cedega here 8 of 10, fully functional but could still
be slightly better.
GUI Front End 8/10 - Codeweavers Total 8/10
Website
Knowledge is power as they say, one of the most important things about
any piece of software you may have is that you fully understand how to use
it. Often times these days ones of the best resources for learning such
information is an application's homepage.
Cedega's home page is relatively horrid to say the least. It does
provide the basic information on the product and pricing but that is about
it. Many parts of the website have been 100% non-functional for the last
months I have had my subscription and it really takes from the product as a
whole. Voting for which applications you wish to be supported is one key
feature that is lacking for example. On top of this another "feature" of
the page is that you cannot view certain data if you do not have a current
subscription - meaning if you are someone looking into Cedega to see if it
will run a certain game you will have to pony up the cash to give it a try.
Also horrid is the Cedega rating system for applications which has three
options: "Certified, Works, and Known not to Work". Certified means you are
able to contact customer service in order to get help with said application
should an issue arise and well the other two kind of explain them self.
Also, and this is not Cedega's fault per-say but odds are is due to a small
user base, but the information about many application in their listing is
rather lacking by comparison to others.
Cedega's website needs some HUGE improvements, as of now it is
functional. So I'll give it a 4 out of 10.
Website 4/10 - Cedega Total 6.7/10
Codeweaver's website is a refreshing change from that of Cedega. It is
obviously that of a professional company, the layout is nice and everything
is clearly labeled. Everything is accessible with or with out a user login.
If you are a member they have a nice system for allowing you to "vote" for
which applications you would like to see better support for (So they know
what they should be spending time working on). The user forums are slightly
non-standard but not necessarily in a bad way, they just take some getting
used to. Also a feature worth noting is Codeweavers ticketing system, you
can browse past support tickets that yourself or other people have posted
for solutions to past issues.
I really do not have anything bad to say about the Codeweavers website,
it is well done and fully functional - 10 out of 10
Website 10/10 - Codeweavers Total 8.5/10
Customer Service/Support
So one of the most important things to know when you are buying
something is that you are going to be able to get support for the product
if it does not work as it is suppose to.
Cedega's customer support is decent. They give you a good response and
help you solve any issues you may be having to a satisfactory amount. How
ever also worth noting is that the only way to get customer support is via
Email. And they only provide official support for their list of forty or so
"certified" games and if you are running certain hardware configuration
(they only support nVidia gfx cards and certain distros). And I feel I
should also mention that their customer service is rather slow to return
emails.
They also how ever have community powered message boards (which they
link from their website) where there are a few very dedicated people who
work hard to help people solve their problems, I found these boards to be a
much faster response than the official email support.
Cedega customer support isn't bad per-say but it also is not anything
exceptional - 7 out of 10
Customer Service/Support 7/10 - Cedega Total 7/10
Codeweaver's provides two different channels of customer support, one
through their wonderful ticket/email system and on their official message
boards. The response time for a ticket I have filed has never been less
than a day, often times if I filed the ticket during normal business hours
I would see a response within a few hours. Their forums also have a few
helpful individuals as well as good number of staff that watch over and do
their best to help out with any issues that may arise while using the
software.
No customer support is perfect but Codeweaver's is darn good to say the
least 9 out of 10
Customer Service/Support 9/10 - Codeweavers Total 8.75/10
Fees and Licensing
I've spent time talking about the ups and downs of these two pieces of
software now - how do you get it? And more importantly how much does it
cost?
Cedega starts at $15 for a three month subscription with varying prices
if you buy for an extended length of time ($45 for a year for instance).
Cedega is yours to install so long as you keep paying for it (after the
subscription runs out you will no longer be able to download Cedega anymore
- meaning if you format you are SOL). Also worth mentioning here is that
the only "demo" Cedega provides is for a single game - Spore. And as I said
above you cannot see the full games data base unless you also pay for it.
So unless you know someone else with a subscription you may very well pay
for it to try a game only to find out doesn't work well. Too be fair though
it's only $15 for the three months, not truly expensive. I personally do
not care for how Cedega licensing works - 6 out of 10.
Fees and Licensing 6/10 - Cedega Total 6.8/10
Codeweaver's CXGames costs $40 for the product and a year's worth of
support and updates. After that it is $35 for a following year of
support/updates and even if you do not renew you still get to continue
using the Codeweavers software you had paid for initially. Now $40 is a
fair bit of cash if you are unsure if something is going to work for you -
however Codeweavers offers a 7 day demo of the full software so you can use
it and see if it works for your needs. Also worth noting is that while
Codeweavers is closed source software they are powered directly by the Wine
project - and as such they give back to it (with code and money). I don't
mind paying a reasonable cost for good software and the fact that they give
some of it back to the Wine project also makes me feel good - 9/10
Fees and Licensing 9/10 - Codeweavers Total 8.8/10
Final Scores - Cedega 6.8 & Codeweavers 8.8
Follow Up
Obviously no piece of software is perfect - these two included - and
while Wine technology has come a long way in the last decade (or so) it
still has a long way to go. As you can see from the numbers and the above
information I prefer Codeweavers to Cedega, come the end of the year I do
not think I will be renewing my Cedega license Which of the two is right
for you is your choice, I just hope my little comparison here may have
presented you with some information on each of them you had not known
before.
Talkback: Discuss this article with The Answer Gang
![[BIO]](../gx/authors/hoogland.jpg)
I am currently a full time student working my way through a math
education program on the south side of Chicago. I work in both theatre &
computer fields currently. I am a huge believer in Linux and believe we
will see Microsoft's dominant market share on the personal computer
crumble at some point in the next twenty years. I write a good deal
about technology and you can always find my most current
thoughts/reviews/ramblings at http://jeffhoogland.blogspot.com/
Copyright © 2010, Jeff Hoogland. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
Quick and Dirty Web Filtering on Linux
By Anderson Silva
Have you ever mistyped a web address and ended up somewhere you
definitely did not want to go? You miss one letter in the URL, and instead
of getting to your favorite site, you end up in the virtual red light
district! So what if instead of you making this mistake, it's your child
accidentally going to these questionable sites? I have two kids, an eight
and a ten year old, and both of them have been actively playing Flash-based
kids' games online since they were two years old. So lately I've been
thinking of solutions to this problem.
There are plenty of non-open-source solutions to help parents filter the
material that their little ones are being exposed to on the web. But I
didn't find that many open source and simple solutions available online.
That's why I decided to explore a couple of different options to solve my
web filtering problem: Squid and Dansguardian.
Using only Squid will get you the very basic functionality to
allow your younger child to access a pretty limited number of sites. If
your kids are a little older, and require a bit more 'freedom' on the World
Wide Web, then skip the next section in this article and jump to Using Dansguardian with
Squid.
Using only Squid:
I've used Squid to set up my system so that my kids' browsers only
access the web addresses that I want them to. Everything else out there is
out of reach for them. In the instructions below, I assume that the Squid
proxy service will be running on the same computer that the children will
be using, but that is not a requirement.
First, let's install Squid on our Fedora system:
su -
yum install -y squid
chkconfig squid on
Next, we edit the file /etc/squid/squid.conf.
1. Find the line on the configuration file with: #Recommendend minimum configuration:
Under that line there will be a few rules starting with the word acl. At
the end of the acl block, add the following line:
acl safekids dstdomain .kidsite.com .kidsite2.com
Replace .kidsite.com and .kidsite2.com with a list of the sites you want
your children to be able to visit. You can list a full address like:
www.kids.com, but then if your child tried to go to a subdomain like
games.kids.com, Squid would block it. Add a dot (.) in front of the domain
to make a wildcard that will allow any subdomain to go through.
2. Find the line: # INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS
Below that line, find the line that says "http_access allow localhost", and comment it out by adding a '#' in front of it:
# http_access allow localhost
3. Above the line http_access deny all, add:
http_access allow safekids
4. Start Squid service:
service squid start
[Optional] 5. If you are going to use Squid on a separate server, open
up port 3128 on your firewall to allow the browser to talk to Squid.
iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 3128 -j ACCEPT
[Optional] 6. Save your iptables settings so it will persist through reboots
service iptables save
Done. This should have your squid proxy server all set up and running.
The major downside of this set up is that it is a lot of manual work to
keep a 'whitelist' of allowable sites for your kids to visit, especially as
they grow older and start needing to use the Internet for school work.
Using Dansguardian with Squid:
So, what's Dansguardian exactly? It is "software designed to control
which websites users can access. It also includes virus filtering and usage
monitoring features." [1] In this section of the article, I will show you
how to get up and running and interacting with Squid, allowing you to add
sites to its banned or exception lists. Dansguardian will use Squid as its
way to communicate with the World Wide Web to filter content.
Installing Dansguardian and Squid on Fedora:
yum -y install dansguardian squid
chkconfig dansguardian on
chkconfig squid on
service squid start
Unlike the previous section Using Squid, we can use the default
installation of Squid. To get dansguardian working in Fedora, there isn't
much work to do either.
First, verify /etc/dansguardian/dansguardian.conf, and make sure you have the following parameters set like this:
# the port that DansGuardian listens to.
filterport = 8080
# the ip of the proxy (default is the loopback - i.e. this server)
proxyip = 127.0.0.1
# the port DansGuardian connects to proxy on
proxyport = 3128
Next start the service:
service dansguardian start
Finally, if you do have firewall rules, open up port 8080 for connection:
iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 8080 -j ACCEPT
And to make it persist across reboots:
service iptables save
You should now be able to configure your web browser to connect to port
8080 and use dansguardian as the proxy on your kids accounts. Be aware that
dansguardian although less restrictive than just using Squid to do web
filtering can still be quite restrictive. If you would like to bypass some
of its rules, and open up some sites for your kids, it's quite simple.
Take a look at the /etc/dansguardian/lists directory and get to
know all the rules that are set out of the box for dansguardian. If you
would like to whitelist a site, edit the file exceptionsitelist and
add the site you'd like whitelisted. Once you are done editing the file,
bounce dansguardian to load the changes.
service dansguardian restart
Configuring the Client:
Now that we have our server set up, we need to set up the child’s
browser to use our dansguardian [or squid] filter:
I will note that this method can be easily be circumvented. I don't
recommend it for computer-savvy older kids, but it should work fine for
your kindergarten to elementary school aged kids. One could always get
fancier and remap ports on the kids machine to directly go to the proxy
making it a bit harder for whiz kids to by pass it.
- Start Firefox (in this case I am using Firefox 2).
- Go to Edit > Preferences > Advanced.
- Select the Network Tab.
- Click "Settings..." under "Connection."
- Under the new "Connection Settings" window, select "Manual proxy configuration."
- For HTTP Proxy, enter the IP of your dansguardian server and port 8080 [or 3216 if only using squid]. If your dansguardian (or even squid) service is running locally on the same machine as the browser, use "localhost."
- Click "OK."
- Close Firefox Preferences.
Now only the sites that meet dansguardian rules will be allowed in, otherwise your kids will get an out of the box message like the image below.
If you have more than one computer set up to connect to a proxy port
other than 8080, like squid's 3128, you can add the following rule to your
proxy server to redirect traffic:
iptables -t nat -A PREROUTING -p tcp --dport 3128 -j REDIRECT --to-port 8080
And then run:
service iptables save
to persist change through reboots.
Overall, this is not a foolproof filter. All you have to do to
circumvent it is turn off the manual proxy on the browser, but I hope that
with my eight and ten year olds, I still have a few years to come up
with a more robust solution.
Talkback: Discuss this article with The Answer Gang
![[BIO]](../gx/authors/silva.jpg)
Anderson Silva works as an IT Release Engineer at Red Hat, Inc. He
holds a BS in Computer Science from Liberty University, a MS in
Information Systems from the University of Maine. He is a Red Hat
Certified Engineer working towards becoming a Red Hat Certified
Architect and has authored several Linux based articles for
publications like: Linux Gazette, Revista do Linux, and Red Hat
Magazine. Anderson has been married to his High School sweetheart,
Joanna (who helps him edit his articles before submission), for 11
years, and has 3 kids. When he is not working or writing, he enjoys
photography, spending time with his family, road cycling, watching
Formula 1 and Indycar races, and taking his boys karting,
Copyright © 2010, Anderson Silva. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
Picking Fruit
By Ken Starks

Having spent a considerable amount of time as a bachelor, I've learned
survival and coping techniques necessary for the lifestyle. I've learned
to buy my own clothes without guilt ("you're not wearing THAT, are you?")
I've conquered the laundromat, microwave, and DVR... I've even mustered the
courage to buy my own food in a supermarket. Exposing testosterone in a
female domain can be tricky, but learn I have...
Look helpless long enough and some woman will show you pity and the cereal
aisle.
But there is one mystery I have yet to unravel.
Melons.
There they sit in the produce section... piles of them, one on top of
another. I have thumped, smelled, hefted, and even squeezed the damned
things. Regardless of my efforts, the one I ultimately bring home will
have the heart of a concrete slab and taste like cardboard.
Precut and packaged melon has been my most often used option.
If only the rest of my life were so simple.
Since 2004, I have been a Linux Advocate. As the founder of The
HeliOS Project, I have organized an effort that, to date, has built
three learning centers and given away approximately 1,071 computers to kids
that cannot afford them. I mention this not to self-promote but to
indicate that I have a bit of experience with New Linux Users.
I've come to realize that picking a candidate for Linux conversion is much
like picking melons from the supermarket... you can thump and inspect to
your heart's content but in reality, not every person is ready for the Free
Software harvest.
Let's look at a couple of the most common factors as to why. The first one
is the most obvious.
Window Glazed

It's a Microsoft Windows world and I don't think anyone wants to argue that
point. Since the advent of Microsoft's last real innovation, Windows 95,
most every computer coming off the production line has come pre-installed
with Microsoft operating systems. People have learned to use their
computers in line with the Redmond Dictate. Let's be honest here:
philosophical arguments aside, when Windows is running well, it is a fairly
decent way to operate a computer. I mean, sure it allows an unsuspecting
user to delete svchost.exe... it even allows a moron to do it multiple times
through multiple reinstalls... but aside from full default user control, it
works mostly well. Mostly.
People get used to doing things one way. Facing another fact, many in the
tech teaching world might agree that about half the people operating a
computer today are not computer operators at all... they are task-set mouse
clickers. Move one icon from its place or slide a toolbar from bottom to
top and many of them will scream ! They have become
comfortable with their chosen applications and environments and are loath
to step outside of them. Even when you physically show someone another
application for the same task, they are often either hesitant or they
openly balk at change. To use another application would mean leaving their
comfort zone.
God forbid.
There is one factor that can change
this... occasionally.
The Pain Threshold

Sometimes, enough is enough. Semi-annual reinstalls and constant losing
battles against viruses and spyware can take its toll. However, I've sat
down at Windows computers that had 5 or 6 spyware toolbars nestled within
Internet Explorer and the owner was clueless as to why his computer was
running slow. Many of these people insist "it's the computer".
Opening the process dialog and showing them the actual software-based
reason for it most often produces glazed-over eyes or blank stares. Seems
that seeing anything ending with a file extension can cause
discomfort... often it's best not to show them the man behind the curtain.
I know that sounds condescending but we
see it more than we'd like to.
Here's the rub...
Many of these people, even if they were willing to try something different,
do not know that they have a choice. Even when they do, I've had first-hand
experience in guiding people to Linux only to have them tell me that a
family member or their "computer friend" said not to
bother... that "Linux Sucks".
Door closed.
Like the rinse-lather-repeat behavior of Microsoft Windows doesn't suck?
I don't apologize for the fact that I believe people who refuse to solve
their own problems are idiots. I've been criticized often for
my lack of bedside manner. Then again, when you have the source of most
Internet and computer security problems suggesting that the computing
public be taxed to clean up infected machines, it's no wonder they are
confused. To many computer users,
Microsoft IS the definitive expert on their computers. This is sad.
In my experience, approximately three out of ten Windows Users in distress
will seriously consider making the switch... and I don't necessarily think
of those as dismal numbers. In the baseball world, that's equal to batting
.300 which can command multi-million dollar annual contracts. I'll take
three out of ten.
Peer Pressure
While we've had most success with this in younger people, the fact that one
harried Windows User recommends Linux to another harried Windows User has
had surprising results. Recently, we installed a Linux computer in a
housing project in East Austin. It was a single-parent household with two
children who needed a computer. It wasn't two weeks until people from the
project were coming over to use that computer to check their email or look
something up on the Internet because their Windows computer was hosed.
Go figure.
We've done nine Linux installs in that project to date and they all stemmed
from that one initial install. Once people have something to physically
compare their current Windows computer to, the job becomes easier.
Pain Threshold indeed.
Kids at school are a big factor in getting us candidates for installs.
While the computer gaming crowd isn't going to pay much attention, having a
kid brag about his "new system" will. The 3D cube has a lot to
do with it, and truth be known, I rarely turn on my extra effects anymore,
but with the younger users, it most certainly is a selling point. Add in
the Atlantis or Cube Gear plugin and you have an environment
that draws them in quickly.
Understanding the Difference

As mentioned above, many New Linux Users are put off or confused by a
different environment. They are so used to the blue XP visuals that when
presented with a differing screen or menu, they become uncomfortable. I've
often mentioned that the absolute worst thing we can do as advocates is to
give a new user a Live CD and walk away. Case in point...
A stay-at-home mom was given a CD by one of our directors a couple
months back. It was carefully explained to her how to use the CD and what
to do in order to get it to boot. When he called her back the next day to
check up on her, she complained loudly that Linux wouldn't work for her.
"I put the CD in, I opened the folder and clicked on every icon in the
box. Nothing happened."
Sigh.
The Director told her to reboot the computer with the CD in the drawer and
it would become apparent what she should do. Nope... the computer BIOS was
set to boot to hard drive first. The boot process took her straight into
Windows again. When it was further explained that she should hit F12 to
change the boot device, she refused.
"If it's that much trouble to use, I don't want to use it."
This is coming from a woman who bitterly complained about the 20 minute
update and patch time she had to endure every time she booted her computer
into Windows.
This from a woman who had 11 individual viruses or instances of spyware on
her machine.
She reported her boot time into a desktop at 6 minutes.
And yeah... sure, most people who sit down at a computer will be able to
negotiate the Live CD just fine, but I am consistently amazed at the number
of people who cannot. I've found that once you personally sit next to them
and show them how it works, their confidence level increases greatly and
the chances of them using Linux on a consistent basis is much better.
I fully realize that many people just do not have the time, patience or
social skills to sit down and walk a new user through this process but many
of us do and that is why I am writing this. Make them comfortable in a new
environment and half the battle is won.
Forewarned is forearmed...
Next? Destroying the mental myths of
Linux use. Stay tooned... this will be fun.
Talkback: Discuss this article with The Answer Gang
![[BIO]](../gx/authors/starks.jpg)
Ken Starks is the Founding Director of The HeliOS Project. The HeliOS
Project rebuilds computers to current technology standards and gives
them to financially disadvantaged children in the Central Texas area. He
lives in Austin, Texas and has been active in other projects such as
Lindependence and The Tux500 project. Ken is a long-time advocate for
the Linux Desktop and has made it the top priority in his life. The
HeliOS Project is entering its fifth year in May of 2010 and to date,
this effort has provided just over 1000 computers to those that need
them most. Ken outlines the mission of his Texas non-profit in simple
terms:
"A child's exposure to technology should never be predicated on
the ability to afford it."
Copyright © 2010, Ken Starks. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
XKCD
By Randall Munroe
More XKCD cartoons can be found
here.
Talkback: Discuss this article with The Answer Gang
![[BIO]](../gx/2002/note.png)
I'm just this guy, you know? I'm a CNU graduate with a degree in
physics. Before starting xkcd, I worked on robots at NASA's Langley
Research Center in Virginia. As of June 2007 I live in Massachusetts. In
my spare time I climb things, open strange doors, and go to goth clubs
dressed as a frat guy so I can stand around and look terribly
uncomfortable. At frat parties I do the same thing, but the other way
around.
Copyright © 2010, Randall Munroe. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
Doomed to Obscurity
By Pete Trbovich
These images are scaled down to minimize horizontal scrolling.
All "Doomed to Obscurity" cartoons are at Pete Trbovich's site,
http://penguinpetes.com/Doomed_to_Obscurity/.
Talkback: Discuss this article with The Answer Gang
![[BIO]](../gx/2002/note.png)
Born September 22, 1969, in Gardena, California, "Penguin" Pete Trbovich
today resides in Iowa with his wife and children. Having worked various
jobs in engineering-related fields, he has since "retired" from
corporate life to start his second career. Currently he works as a
freelance writer, graphics artist, and coder over the Internet. He
describes this work as, "I sit at home and type, and checks mysteriously
arrive in the mail."
He discovered Linux in 1998 - his first distro was Red Hat 5.0 - and has
had very little time for other operating systems since. Starting out
with his freelance business, he toyed with other blogs and websites
until finally getting his own domain penguinpetes.com started in March
of 2006, with a blog whose first post stated his motto: "If it isn't fun
for me to write, it won't be fun to read."
The webcomic Doomed to Obscurity was launched New Year's Day,
2009, as a "New Year's surprise". He has since rigorously stuck to a
posting schedule of "every odd-numbered calendar day", which allows him
to keep a steady pace without tiring. The tagline for the webcomic
states that it "gives the geek culture just what it deserves." But is it
skewering everybody but the geek culture, or lampooning geek culture
itself, or doing both by turns?
Copyright © 2010, Pete Trbovich. Released under the
Open Publication License
unless otherwise noted in the body of the article. Linux Gazette is not
produced, sponsored, or endorsed by its prior host, SSC, Inc.
Published in Issue 173 of Linux Gazette, April 2010
The Linux Launderette
[hsi@dhs.gov: Department of Homeland Security]
Ben Okopnik [ben at linuxgazette.net]
Sat, 13 Mar 2010 14:55:12 -0500
Wow, got to give these spammers props for relevance and scope; too bad
they're wasting it on such small potatoes. Even their URL is so cute
that I'm going to leave it unmangled. The English is quite amusingly
mutilated ("has received the prevention", "about the occurred shift",
"Earth's figure axis", etc.), but it all makes enough sense that
somebody is sure to fall for it. Amazing.
----- Forwarded message from hsi@dhs.gov -----
Date: 11 Mar 2010 18:19:12 -0000
From: hsi@dhs.gov
To: ben@linuxgazette.net
Subject: Department of Homeland Security
Department of Homeland Security
INTELLIGENCE BULLETIN
UNCLASSIFIED
11 March 2010
Yesterday the Department of Homeland Security has received the
prevention from NASA's Jet Propulsion Laboratory about the occurred
shift of Earth’s figure axis:
The recent Chilean earthquake shifted the axis by approximately three
inches and shortened the length of a day by 1.26 microseconds. According
to NASA’s Jet Propulsion Laboratory the displacement of Earth’s axis
will cause natural disasters on the Eastern coast of the USA including
Florida, Georgia, South and North Carolina.
In this connection the DHS has made a decision to prepare for general
evacuation from the specified area. The population of the region should
be ready for evacuation. It is necessary collect valuable possessions,
documents, things of first necessity, and wait for the announcement.
In order to prevent panic among the population DHS asks to stay calm and
follow the official instructions listed below:
http://dhsorg.org/docs/instructions.zip
U.S. Department of Homeland Security
Washington, DC 20528
----- End forwarded message -----
--
* Ben Okopnik * Editor-in-Chief, Linux Gazette * http://LinuxGazette.NET *
Phoneutoo spam
Neil Youngman [ny at youngman.org.uk]
Mon, 1 Mar 2010 15:59:33 +0000
I assume this is a targeted spam, not an official Gazette communications
channel?
"Linux Gazette has added you to their group, using Phone U Too, so you can
begin receiving important voice and email notifications related to Linux
Gazette."
[ Thread continues here (11 messages/12.25kB) ]
Talkback: Discuss this article with The Answer Gang
Published in Issue 173 of Linux Gazette, April 2010




 Debian Kernel Vulnerabilities Being Patched
Debian Kernel Vulnerabilities Being Patched

![[BIO]](../gx/authors/dokopnik.jpg)

 A. N. Onymous has been writing for LG since the early days - generally by
sneaking in at night and leaving a variety of articles on the Editor's
desk. A man (woman?) of mystery, claiming no credit and hiding in
darkness... probably something to do with large amounts of treasure in an
ancient Mayan temple, and a beautiful dark-eyed woman with a snake tattoo
winding down from her left hip. Or maybe A.N. is just into privacy. In
any case, we're grateful for the contributions.
A. N. Onymous has been writing for LG since the early days - generally by
sneaking in at night and leaving a variety of articles on the Editor's
desk. A man (woman?) of mystery, claiming no credit and hiding in
darkness... probably something to do with large amounts of treasure in an
ancient Mayan temple, and a beautiful dark-eyed woman with a snake tattoo
winding down from her left hip. Or maybe A.N. is just into privacy. In
any case, we're grateful for the contributions.![[BIO]](../gx/authors/brownss.jpg) Silas Brown is a legally blind computer scientist based in Cambridge UK.
He has been using heavily-customised versions of Debian Linux since
1999.
Silas Brown is a legally blind computer scientist based in Cambridge UK.
He has been using heavily-customised versions of Debian Linux since
1999.
![[BIO]](../gx/authors/grebler.jpg)
 Have a look at this picture. I swear that it's for real. It popped up
on more than one occasion on my company laptop. I don't know
whether it came from XP, some other piece of Microsoft software, or
some other software altogether. But it just beggars belief!
Have a look at this picture. I swear that it's for real. It popped up
on more than one occasion on my company laptop. I don't know
whether it came from XP, some other piece of Microsoft software, or
some other software altogether. But it just beggars belief!
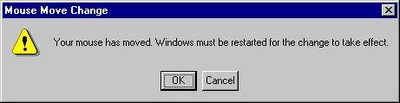
![[BIO]](../gx/authors/hoogland.jpg)
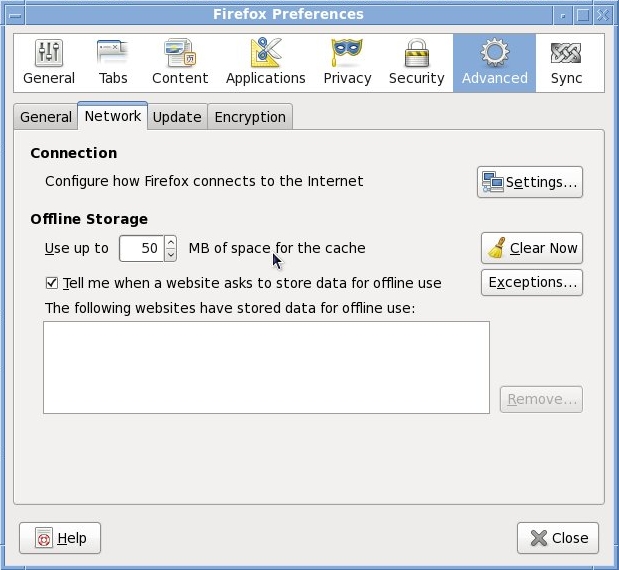
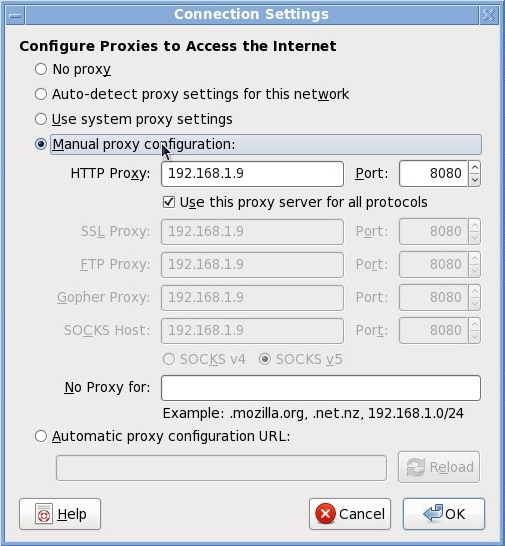
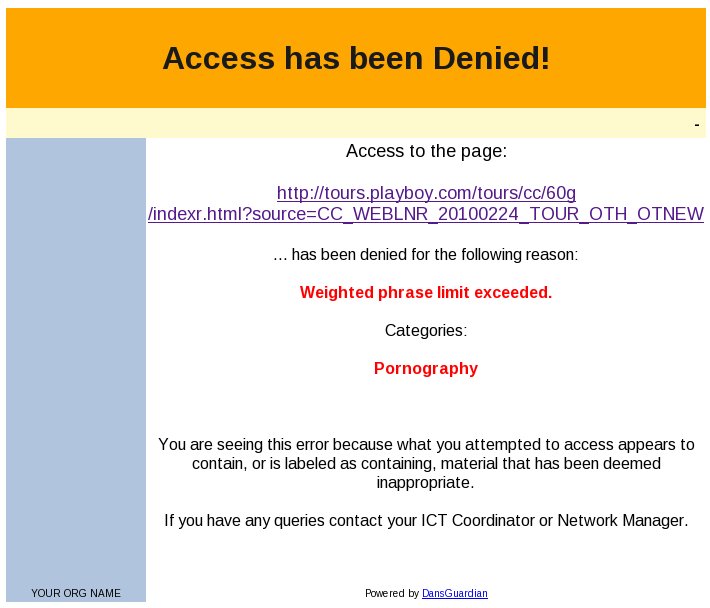
![[BIO]](../gx/authors/silva.jpg)





![[BIO]](../gx/authors/starks.jpg)
![[cartoon]](misc/xkcd/geoip.png)
![[cartoon]](misc/xkcd/devotion_to_duty.png)